Cloud computing is no longer a new and emerging technology. These days, all manner of businesses routinely rely on the cloud to store, manage, and access their data. Many more rely on the cloud to provide business-critical Software-as-a-Service (SaaS) capabilities. And more fundamentally still, a growing number use the cloud to house business-critical servers and other virtual machines. Rightly, too, cloud data centres are regarded as more secure and resilient than on-premise infrastructure. But that doesn’t mean that businesses can forget about security when it comes to the cloud: far from it. So how secure is cloud computing and what do you need to consider?
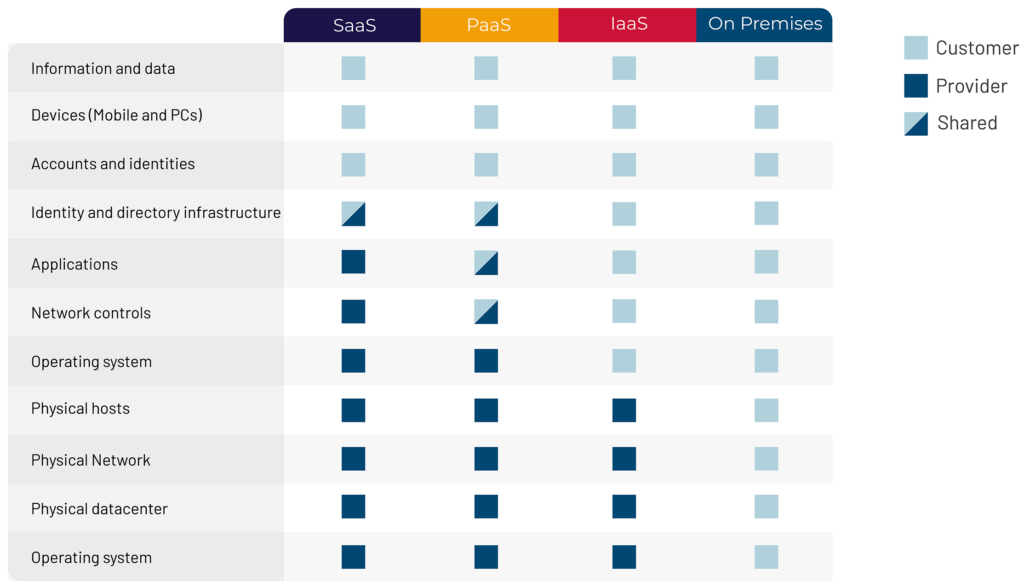
Well, while cloud service providers handle some aspects of security, they don’t handle all aspects of security. It’s important to realise that you, the customer, are also responsible for aspects of security.
This gives rise to several challenges.
Cloud security misunderstandings
First, there’s often confusion about cloud service providers’ overall responsibility for security. Indeed, it’s not unknown for some businesses to think that their cloud service provider is handling everything, with the business itself responsible for nothing.
Second, even when businesses understand that cloud service providers take care of only some aspects of security, and that they the customer are responsible for other aspects, there can often be confusion about who exactly is responsible for what. The result: vulnerability gaps, where businesses erroneously imagine that their cloud service provider is taking care of something that they aren’t.
And third, even when that confusion doesn’t exist, or has been ironed out, businesses may simply be unclear or uncertain about how they should properly protect themselves. Security within the four walls of the business is one thing, and security in a hybrid on-premise/ cloud environment is quite another.
And let’s be clear: every business that’s using cloud services is hybrid. If you have an end-point in the business (and you will), then securing that end-point is your responsibility. Because if it’s left unsecured, it can undoubtedly threaten the integrity of the data and systems in the cloud.