Identifying Compromise
There are several Indicators of Compromise (IOCs) in key areas that we can look for to identify a breach.
Sign-in Logs
- Impossible travel: Sign ins within a short span of time from different geolocations that are not probable for normal travel.
- Device/User-agent: Monitoring the device and user-agent associated with a sign in can be a good indication of compromise. If a sign in is not on a registered device and not one that the user uses or should be accessing their account on can be a potential red flag.
- Access to the following Applications/resources:
- Office365 Shell WCSS-Client’ (indicative of browser access to Office365 applications)
- ‘Office 365 Exchange Online’ (indicative of post-compromise mailbox abuse, data exfiltration and email threats proliferation)
- ‘My Signins’ (used by attackers for MFA manipulation)
- ‘My Apps’
- ‘My Profile’
- IP Addresses: IP Addresses can tell us a large amount of information, a basic investigation using open-source tools can tell us if the IP relates to a VPN, the Geolocation information, and the general reputation, giving us insights into the legitimacy of the sign in.
- Suspicious Failed & Successful Sign ins: A large number of failed sign ins followed by a successful sign-in can indicate brute forcing of passwords to gain access to an account. A single successful sign-in is usually indicative of phishing being used to compromise an account.
Audit Logs
A user’s audit logs can tell us a host of information regarding what actions a user is taking. The two main areas of interest are the Entra Audit log and the Unified Audit Logs. Entra Audit logs will show us what Entra actions have been taken by an account such as password resets, MFA registration, Application registrations.
The Unified Audit Log provides more information in regards to all actions taken by a user such as the adding or removing of mailbox permissions, any synchronisation events, email deletions, and SharePoint access. These logs provide a wealth of information to help us identify any activity that may have taken place which is out of the ordinary.
Mailbox
New Rules: Aspire have found that adversaries will often create several malicious rules are created with the name “.”, “..”, “…” which will usually mark select emails as read and filter them into the “RSS Feeds” or “Conversation History” folder. In our experience, these are often malicious but can also point us to further accounts to investigate.
The benefit of an adversary taking this action is due to these folders being default folders within Outlook that most users will not often access. So, no visual changes will occur to the compromised user. The adversary can then control communications between selected users and hijack emails they find valuable.
Emails
Within a user’s emails is usually where we can find our initial access through phishing. To identify these ourselves we must understand what they may look like:
Example One: Typo-squatted Domains
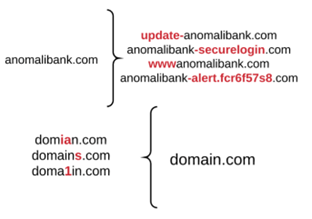
Example from https://www.researchgate.net/figure/Typosquatting-Examples_fig2_321233558
These domains are used to spoof legitimate websites or emails to impersonate a specific user. These are usually small modifications to a legitimate domain, as seen in the example above.
Example Two: Legitimate Email/Suspicious Links
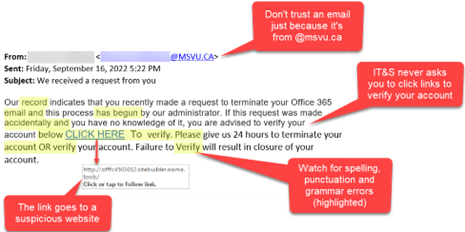
Example of a legitimate email being used with a suspicious link.
Recommendations
- Email Filtering and Anti-Phishing: Deploy solutions to identify and block phishing emails, malicious attachments, and suspicious links. Regularly update and configure for evolving threats.
- Email Authentication: Implement SPF, DKIM, and DMARC to prevent email spoofing and enhance security.
- External Email Banner: Apply a banner to all externally received emails, informing of the threat they could bring and make use of a “First Contact Safety Tip” informing the user that this is the first contact from that email, preventing email hijacks from typo-squatted domains.
- Multi-Factor Authentication (MFA): Implement MFA for email accounts and critical applications to add an extra layer of security. Require something they know (password), something they have (verification code/token), and optionally something they are (biometric data). For privileged accounts phishing resistant MFA can be enabled, this will show the user where their sign in attempt is being used to further confirm that a sign-in is legitimate.
- Access Control and Privilege Management: Limit access to sensitive data and systems. Use MFA for critical systems and regularly review and update user access.
- Conditional Access: Define and enforce access policies based on conditions and user attributes. Include policy definition, user authentication, device compliance checks, IP geolocation, risk-based assessment, Azure AD integration, and real-time monitoring/reporting.
- Regular Security Audits: Conduct audits and vulnerability assessments. Update and patch software regularly.
- Employee Training: Provide cybersecurity training to increase awareness of threats like phishing, malware, and social engineering. Train employees to recognise and report suspicious emails.
- Entra Configuration: Several settings in Entra can be configured to prevent normal users from taking typically administrator actions such as registering applications, creating tenants, viewing the admin centre, and guest account permissions. These are often not configured by default and should be reviewed to ensure security.
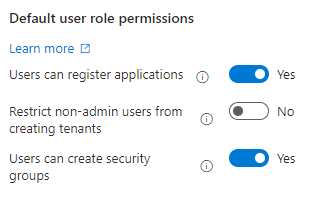
- Principle of Least Privilege: Ensure only accounts that require elevated permissions have them, and where possible, ensure these accounts do not have mailboxes to prevent phishing attempts.
- Logging and Alerting: Ensuring that a logging and alerting solution is in place in critical in detecting and remediating potential malicious events. Using a SIEM and 365 monitoring compromises can be alerted to and remediated as and when it happens. Should any indication of compromise be detected, it is alerted to and remediated immediately.