Executive Summary
The Aspire Security Operations Centre (SOC) monitor thousands of customer endpoints and has ingested over 1.9B events (Yes, billion!) into our Security Information & Event Management System (SIEM). Monitoring 24×7, we stay up to speed with the latest threats targeting organisations in various industries and verticals.
One Achilles heel for most organisations is securing and protecting Office 365 from Business E-mail Compromise and Data Loss. Whilst monitoring this particular technology, we have uncovered a very targeted campaign, specifically targeting directors in the victim business.
Whilst this is quite commonplace, our investigation exposed a phishing kit utilising session hijacking to gain access to the recipient’s Office 365 account.
Our 24×7 SOC team responded by producing a list of actionable Indicators of Compromise (IOC’s) that can help identify further targets and campaigns.
We are sharing the following analysis to serve as an awareness warning to readers on how sophisticated Business E-mail Compromise can be.
How this campaign works
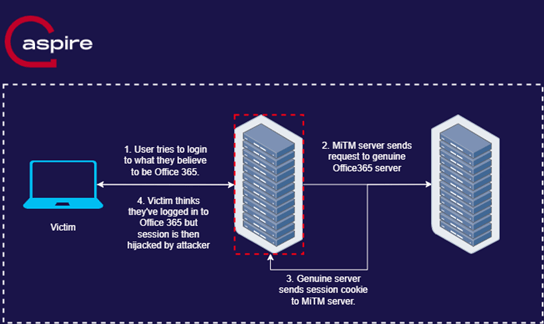
- The victim receives a phishing e-mail, either with a link or attachment. This takes them to what looks like their organisation’s genuine 365 login page, with the branding and their e-mail already in, just asking them to enter their password to log in.
- The Man-in-the-Middle (MiTM) server is handling these requests, by capturing the requests and sending them to the genuine Office 365 server. This means that it can see all data sent from the victim and 365.
- Once the user enters their credentials, the MiTM server will then capture the session cookie sent from the genuine Office 365 server.
- It then appears as if the user has logged in as normal, but the attacker can now use that session cookie to access the organisation’s 365, including the victim’s mailbox and continue with the campaign by sending e-mails to payroll, for example.
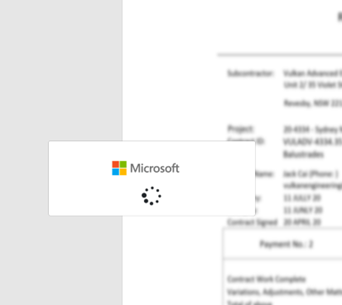
When the victim opens the attachment or link, it will look like quite an un-sophisticated lure:
After a couple of seconds, this then appears to be a genuine 365 login page:
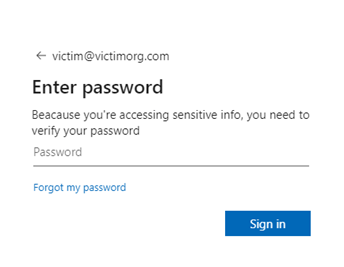
We’ve redacted the victim organisations’ domain and logo from the above screenshot.
Our 24×7 SOC team further analysed the malicious code in the phishing kit, which uncovered a phishing kit called Evilginx2. A list of indicators of compromise has been provided below for you to check your own environment, though we envisage these indicators will change often to evade basic detection:
Check your Azure AD Sign-In logs for login attempts from:
- 52[.]70[.]26[.]73
- 35[.]175[.]223[.]210
Monitor high-profile users in your environment for rare subject lines and senders:
- SYSTEM MAIL ruthe85717[@]icloud[.]com
Monitor for suspicious geographical logins (Landspeed anomalies/Impossible Travel)
- 52[.]70[.]26[.]73 is hosted in USA – Our victim user was already logged in from the UK.
- 35[.]175[.]223[.]210 is also hosted in USA and is a known Tor Proxy Node.
Monitor for suspicious attachment extensions:
- .html attachments
How to protect your organisation from these campaigns
Managed Detection & Response service
There are many added benefits to having a managed detection & response service, Aspire can provide you with a fully managed Endpoint Detection & Response service with additional Office 365/Azure Active Directory monitoring 24x7x365.
Our SOC stays ahead of threats and proactively communicates what they’ve identified and what action they’ve taken to remediate the threat in your environment.
User Awareness Training & Phishing Simulations
Aspire can provide best-in-class phishing simulations, that are fair, informative and representative of the current threat landscape. Our SOC can provide you with prescriptive advice on how to improve your user awareness posture.
Hardening controls
Aspires professional services can provide you with peace of mind by auditing your environments for the necessary controls required to harden your environment against the latest threats.